Authentication
The UPAM Authentication application is used to monitor and configure authentication for wired and wireless devices.
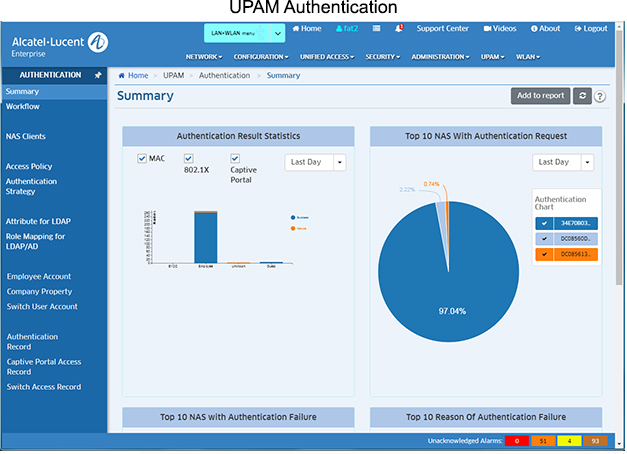
The following screens are used to monitor and configure the Authentication application:
- Summary - Provides an overview of authentication activity for the network.
- Workflow - Authentication application workflows provide system-defined workflows that can be used to create wired or wireless service for both employees and guest users
- NAS Clients - Used to configure NAS Clients. A client connects to the NAS, and the NAS then connects to a AAA Server to determine whether or not the client’s supplied credentials are valid
- Access Policy - Used to configure Authentication Access Policies. Authentication Access Policies are used to define the mapping conditions for an authentication strategy.
- Authentication Strategy - Authentication Strategy is used to set up a user profile source and login method (web page or not) for authentication, as well as the network attributes applied after passing the authentication.
- Role Mapping for LDAP - Authentication Role Mapping enables you to assign different Access Role Profiles and Policy Lists to different sub-user groups by creating mapping rules based on user attributes.
- Employee Account - Used to create login accounts for employee users in the local UPAM Database.
- Company Property - Used to create a Company Property List containing information on devices owned by a company and assigned to an employee (e.g., printers, IP phones, laptops, tablets).
- Switch User Account - Used to configure user Authenticated Switch Access through UPAM.
- Authentication Record - Displays authentication information for all devices authenticated through UPAM.
- Captive Portal Access Record - Displays captive portal information for all devices authenticated through UPAM.
- Switch Access Record - Displays information about user authentication access to network switches.

