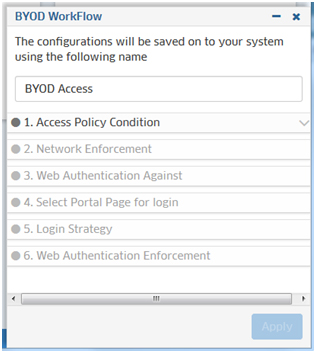
Authentication application workflows provide system-defined workflows that can be used to create wired or wireless service for both employees and guest users, supporting company devices as well as BYOD devices. Select a workflow (e.g., BYOD Access with MAC and Captive Portal ), click on Begin Now, and complete the steps in the workflow. When you have completed all of the steps, click on the Apply button at the bottom of the workflow to complete the configuration. The BYOD Access with MAC and Captive Portal Workflow is shown below. The configuration process is the same for all workflows.

Workflows can be used to configure:
The BYOD Access Workflow uses UPAM to authenticate BYOD users using MAC Address and Captive Portal against a local or external database.
Complete the steps as described below, then click on the Apply button.
The Guest Access Workflow uses UPAM to authenticate Guest Users using MAC Address and Captive Portal against the Guest Account Database.
Complete the steps as described below, then click on the Apply button.
The MAC or 802.1x Authentication Workflow uses UPAM to authenticate users using MAC authentication or 802.1x authentication against a local or external database without Captive Portal.
Complete the steps as described below, then click on the Apply button.