Guest Access
Strategy
The Guest
Access Strategy Screen displays information about configured Guest Access Strategies and is used to configure access attributes for guest
users. The screen can be used to create, edit,
and delete Guest Access Strategies. There is a
pre-configured Default Guest Access Strategy that you can edit, or you can
create new Guest Access Strategies (up to a maximum of 32).
Creating a Guest
Access Strategy
Click on the Add icon and complete the fields as described below. When you are finished, click on the Create button.
General
Configure redirect and authentication attributes.
- Strategy
Name - The Guest Access Strategy Name.
- Redirect
Strategy - The captive portal page
template used for guest user login.
- Mode - The http protocol used to redirect the captive portal page (https/http).
- IP/FQDN - The displayed URL format for redirection to the captive portal page (FQDN/IP).
- Current FQDN - The FQDN used for the captive portal page redirection.
- Authentication
Resource - The guest user profile
database, which is the local UPAM database (Local Database). Guest user
accounts can be added on the UPAM - Guest Access - Guest Account Screen.
Login Strategy
Configure guest user login.
- Login
By - Specify the login method:
- Username
& Password - Guest user login by their
credential (Username and Password).
- Terms
& Condition - Guest user login by accepting
the Terms and Conditions. When this login method is selected, additional Registration Strategy
information is required.
- Access
Code - Guest user login by a
unified access code.
- Simple Persona - Guest user login by email address. When this login method is selected, additional Registration Strategy information is required.
- Reset Password - If enabled, this option allows a guest user to change their login password without Administrator operation. Select one of the options from the drop-down to allow the guest to receive a Verification Code through e-mail, SMS, or both. The user will be able to click on the "Forget Password?" link on the login screen for their account to request a Verification Code to change their password.
- Social
Media Account - Guest user login by social
media account (Facebook, Google, Rainbow, WeChat). Complete the fields below for
social media login. Note that you must also configure the Social Login
Settings in an Access Role
Profile for the applicable Social Media account (Facebook, Google, Rainbow, WeChat).
-
Portal
Server Domain - Social Media website domain.
Domains must be entered in Fully Qualified Domain Name (FQDN) format
(e.g., www.upam.com). Note that you must configure your local DNS Server
to resolve this Hostname to the correct UPAM IP address.
- Facebook
OAuth Client ID - The OAuth Client ID provided
by Facebook (see Configuring the Facebook
API for more information).
-
Google
Plus OAuth Client ID - The OAuth Client ID provided
by Google (see Configuring the Google API for more information).
- Rainbow OAuth Client ID - The OAuth Client ID provided
by Rainbow (see Configuring the Rainbow API for more information).
- WeChat Open APP ID - The WeChat APP ID provided by the WeChat Official Accounts Platform (see Configuring the WeChat API for more information).
- APP Secret - The APP secret key for the wireless service provider.
- Success
Redirect URL - Specify the redirect URL for
the browser after the guest user passes captive portal authentication:
- None
- No redirect URL. Remain on the “Success” login page
configured by the Administrator.
- Go
to Initial URL - Redirect to the
guest-user-input URL after passing authentication.
- Go
to Fixed URL - Redirect to a fixed web page
specified by the Administrator.
- Custom Attributes - Allow the Administrator to customize the attributes for guest self-registration to collect the guest user information. The Administrator can configure up to 20 attributes (max length 32 characters each). The configured attributes will be displayed in the self-registration page where the guest user can input 1 - 255 character(s) for each attribute. To make this option visible for configuration, the login method must be specified in the Terms & Conditions.
Note: If you are configuring Custom Attributes, then the Administrator can get all user information in the Captive Portal Access Record.
Note: If
you are configuring Social
Media Login you must configure and obtain Google and Facebook tokens using the Google and Facebook
Developer APIs as detailed below.
Registration Strategy
The following Registration Strategy fields are required when "Terms & Condition" or "Simple Persona" is selected as the user login method. This section is not displayed for the other login methods (Username & Password, Access Code).
- Remeber Device - Specify whether to remember the device MAC address and make it valid after successful authentication (Enabled/Disabled). If the remembered device is valid, the MAC address check will be performed first and the device allowed access without re-authentication.
- Period Unit - The unit used for the Account Validity Period Attribute (Days, Hours, Minutes).
- Device Validity Period - The length of time that the user device is valid. This value is entered based on the selected Period Unit. For example, if Days is selected, enter the number of days the user device is valid; if Hours is selected, enter the number of hours, etc. By default, Days = 30, Hours = 24, and Minutes = 60.
Post Portal
Authentication Enforcement
Configure post-authentication enforcement for guest users.
- Fixed
Access Role Profile - The Access Role Profile
assigned to the guest user after passing authentication (required for AOS Switches).
- Fixed
Policy List - The Policy List assigned to the
guest user after passing authentication.
- Data Quota Status - Specify whether to control guest access based on user data quota (Enabled/Disabled). If enabled, the Data Quota limit is applied only to a user who logs in with user name and password credentials. It will not be applied to a user who logs in with an access code or a user who just accepts the terms and conditions.
- Quota Exhausted URL - The redirect URL to which the accessing device will be guided after the user reaches their data quota limitation.
- Other Attributes - Select an attribute from the drop-down, enter a value and click on the Add icon to add the attribute. Repeat the process to add additional attributes.
- Session Timeout - The Session Timeout Interval is the maximum number of consecutive seconds of connection allowed to the user before termination of the session or prompt. If not configured, the device’s default session timeout policy will take effect. (Range = 12000 - 86400, Default = 43200)
- Accounting Interim Interval - Interval for RADIUS accounting, in seconds. If not configured, the device’s default accounting policy will take effect. (Range = 60 - 1200, Default = 600)
- WISPr Bandwidth Max Up - The user upstream bandwidth, in kbit/s. By default, it is not limited.
- WISPr Bandwidth Max Down - The user downstream bandwidth, in kbit/s. By default, it is not limited.
- Alcatel-Device-Psk - The device PSK Passphrase used for authentication.
Self-Registration
Strategy
Configure the self-registration attributes for guest user login when the
guest user is required to perform self-registration and approval before
accessing the network. In this case, the guest user account is automatically
created and send to the guest user through e-mail by UPAM. The
self-registration strategy is only applicable for login by Username and
Password.
- Self-Registration
- Enables/Disables the self-registration function.
- Account
Name Created By - The field from which the guest
user account is retrieved, the information is entered by the guest user in
the self-registration login page:
- Guest
Name - Login account for the guest
user
- Email
Address – Email address of the guest
user
- Phone
Number - Phone number of the guest
user.
- Password
Creation - Password creation method:
- Manually
- Password for guest user account is set by guest user
in the self-registration web page.
- Automatically
- Password for guest user account is automatically
generated by UPAM and sent to guest user through E-mail.
- Success Account Notification - If enabled, the user must specify an e-mail address as part of the Self-Registration Strategy, and the login details are sent to the user.
- Approval
- Specify whether the guest registration request is
required to be approved by a sponsor in the company or a guest operator. The employee sponsor could be
an Administrator or employee the guest going to visit.
- Disabled
-
Approval by an employee or guest operator in not required.
- Approved
by Employee Sponsor -
Approval by an the employee specified in the Self-Registration Request Screen is required.
- Email
Suffix Restriction -
Enter the employee sponsor e-mail suffix(es) and click on the Add icon. This is the e-mail suffix used by the company employee, which will be combined with a specific employee e- mail ID to form a full e-mail address. The registration request will be sent to this e-mail address.
- Full Email
- Enter the full employee e-mail address.
- Approved
by Guest Operator -
Approval by a guest operator specified on the Guest Operator Screen is required.
- Location-Based Notification - Enables/Disables location-based notification. When enabled, send the guest request to guest operators for the specific location. When disabled, send the guest request to all operators.
- Required
Attributions - Customize the information
fields that the guest user is required to input during self-registration. Certain fields are required and pre-configured for employee sponsor or guest operator approval.
- Guest
Name - Login account for the guest
user.
- Password
- Login password for the guest user. If the password
creation method is set to “Automatically”, the guest user does not have
to enter this field.
- Full
Name - Full name of the guest user.
- Email
ID- Email address of the guest
user.
- Phone
Number - Phone number of the guest
user.
- Company
- Name of the company the guest user is representing.
- Position
- Position of the guest user in their company.
- Department
– Department of the guest user in their company.
- Country
or Region - Country or region of the guest
user’s company.
- Employee
Visited - The employee being visited by
the guest user.
- Employee
Email ID - Email address of the employee
being visited.
- Employee
Phone Number - Phone number of the employee
being visited.
- Reason
Visited - The purpose of the guest
user’s visit.
- Custom Attributes - Allow the Administrator to customize the attributes for guest self-registration to collect the guest user information. The Administrator can configure up to 20 attributes (max length 32 characters each). The configured attributes will be displayed in the self-registration page where the guest user can input 1 - 255 character(s) for each attribute.
- Authorize By Verification Code - If the e-mail or phone number is required, Enables/Disables whether to send a verification code to specified address to ensure the e-mail or phone number is correct.
- Password Visibility - Enables/Disables whether to display account information such as name and password on the Registration Result Page.
- Service Level - When Service Level is set to "None", settings of Registration Strategy in Global Configuration will take effect for guest self registration.
Note: If you are configuring Custom Attributes, then the Administrator can get all user information in the Guest Account, Self-Registration Request, or via a guest operator email.
Service Level
(Optional)
Configure the different service levels for the guest account by binding
various levels of Access Roles and Policies. The guest user can select an
appropriate service level when logging into the network. Enable and configure applicable Service Levels as described in the Service Level section of Global Configuration.
WiFi4EU
WiFi4EU provides free access to public Wi-Fi in parks, schools, public buildings, and health centers throughout Europe.
-
WiFi4EU - Enables/Disables WiFi4EU. To use the WiFi4EU feature, the “RedirectStrategy“ must use the specified WiFi4EU template for the Captive Portal page. In addition, the validity period for Captive Portal authentication must be no more than 24 hours per the WiFi4EU requirement. This value can be changed in Registraton Strategy from the Global Configuration screen.
- Network Identifier - The Network Identifier received from the WiFi4EU portal as part of the Installation report.
- Self Test Modus - The WiFi4EU portal self-test mode.
Editing a Guest
Access Strategy
Select a strategy in the Guest Access Strategy List and click on the Edit
icon. Edit any fields as
described above and click on the Apply button. Note that
you cannot edit the Strategy Name.
Deleting a Guest
Access Strategy
Select a strategy(ies) in the Guest Access Strategy List and click on the
Delete icon. Click OK at the Confirmation
Prompt. You cannot delete the Default Guest Access Strategy.
Guest Access Strategy List
- Strategy Name - The Guest Access Strategy name.
- Redirect Strategy - The captive portal page template used for guest user login.
- Mode - The http protocol used to redirect the captive portal page (https/http).
- IP/FDQN - The displayed URL format for redirection to the captive portal page (FQDN/IP).
- Authentication Resource - The guest user profile database, which is the local UPAM database (Local Database).
- Login By - User login method (e.g., Username & Password, Social Media Account).
- Social Media Account - Indicates whether Social Media login is enabled/disabled.
- Portal Server Domain - The Social Media website domain.
- Facebook OAuth Client ID - The OAuth Client ID provided
by Facebook.
- Facebook Authorized Origins - The Facebook Authorized Origins URL that is copied into the Valid OAuth redirect URLs field when configuring the Facebook API.
- Google OAuth Client ID - The OAuth Client ID provided
by Google.
- Google Authorized Origins - The Google Authorized Origins URL that is copied into the Authorized redirect URLs field when configuring the Google API.
- Success Redirect URL - The redirect URL for the browser after the guest user passes captive portal authentication.
- Fixed URL - The redirect URL to a fixed web page
specified by the Administrator, if applicable.
- Fixed Access Role Profile - The Access Role Profile assigned to the guest user after passing authentication.
- Fixed Policy List - The Policy List assigned to the guest user after passing authentication.
- Session Timeout Interval - The maximum number of consecutive seconds of connection allowed to the user before termination of the session or prompt. If not configured, the device’s default session timeout policy will take effect.
- Accounting Interim Interval - Interval for RADIUS accounting, in seconds. If not configured, the device’s default accounting policy will take effect. (Range = 60 - 1200, Default = 600)
- Upstream Bandwidth - The user upstream bandwidth, in kbit/s. By default, it is not limited.
- Downstream Bandwidth - The user downstream bandwidth, in kbit/s. By default, it is not limited.
- Self-Registration - The administrative state of guest user self registration (Enabled/Disabled).
- User Name Created By - Method used to create an account name for the guest user in the self-registration workflow.
- Password Creation - Whether the password for the Guest User Account is set by the user "Manually" on the self-registration page or "Automatically" generated by UPAM and sent to the user via e-mail.
- Approval - The administrative state of the approval requirement for a guest registration request (Enabled/Disabled).
- Full Email Address - The full employee e-mail address if approval is required.
- Required Attributes - Information the guest user is required to input during self-registration.
- Password Visibility - The administrative status of password visibility on the Registration Result page (Enabled/Disabled).
- Location-Based Notification - Administrative status of Location-Based Notification (Enabled/Disabled).
- Remeber Device -Indicates whether the online device was remembered by UPAM and added into the Remembered Devices List.
- Data Quota Status - The administrative state of the data quota limitation (Enabled/Disabled).
- Quota Exhausted URL - The redirect URL to which the accessing device will be guided after the user reaches their data quota limit, if applicable.
- Service Level - The service level defined in the self-registration strategy. If the service level in Global Configuration is disabled or the service level assigned to the strategy is disabled, the service level content in table and detail will be marked in red color “Disabled”.
- Reset Password - The User Reset Password administrative status (Enabled/Disabled). If enabled, the user can reset their Guest Account password without Administrative action.
Configuring Facebook, Google, Rainbow, and WeChat Developer APIs for Social Login
The sections below provide detailed instructions for configuring the Facebook, Google , Rainbow, and WeChat APIs and obtaining the necessary tokens for Social Login.
Configuring the
Facebook API
1. Go
to https://developers.facebook.com/apps.
Click on the Create New
App button to bring up the Create a New App ID window. Enter
the Display Name (e.g., UPAM) and your Contact
Email and click on the Create
App ID button.
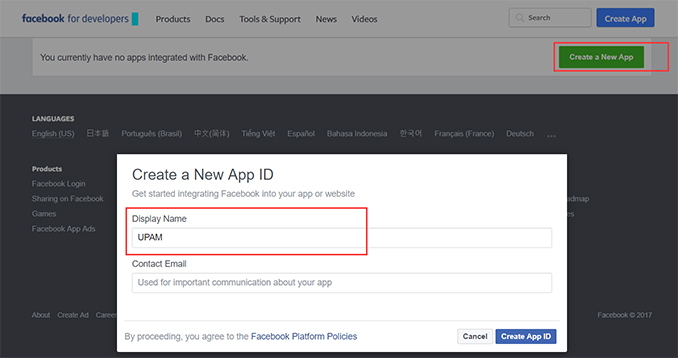
2. Click on Settings - Basic in the Navigation Tree on the left side of the screen to display the basic App
settings.
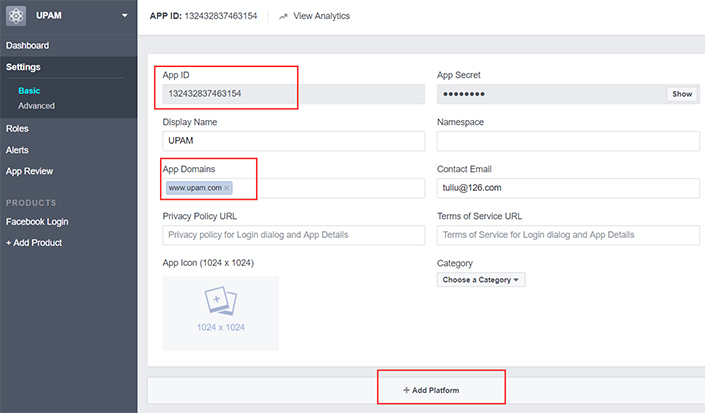
3. Click on the + Add
Platform button at the bottom of the screen to bring up the
Select Platform Screen.
4. Click on Website.
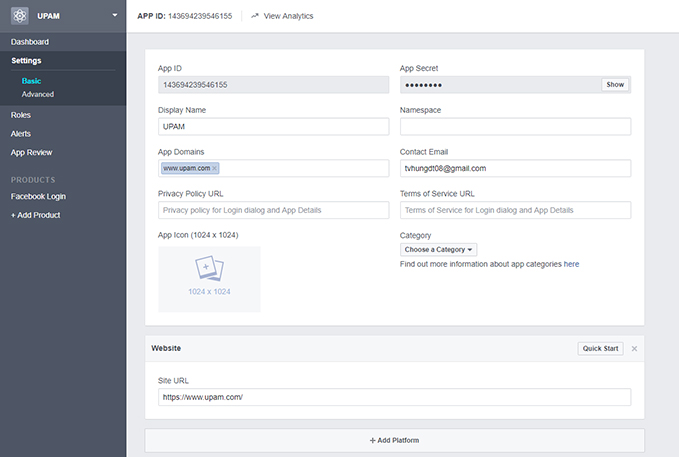
5. Complete
the App Domain and Site URL Fields as follows, then click on the Save Changes button.
- App
Domains - Enter the Portal Server Domain
you entered in your Guest Access Strategy (e.g., www.upam.com )
- In
Site URL: Enter the full web URL
(e.g., https://www/upam.com/)
6. Go
to the Guest Access Strategy Screen in OmniVista (UPAM - Guest Access - Guest
Access Strategy).
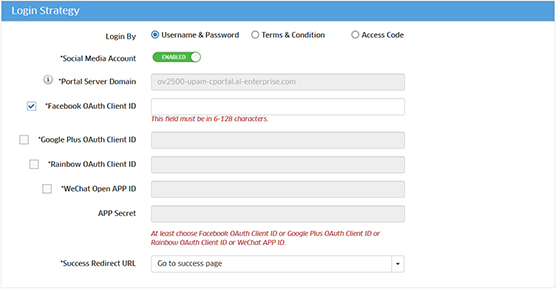
7. In the Facebook OAuth Client
ID field, enter the App ID you received from Facebook.
8. Return
to the Facebook API Configuration Screen and click on Facebook Login - Settings
in the Navigation Tree on the left side of the screen.
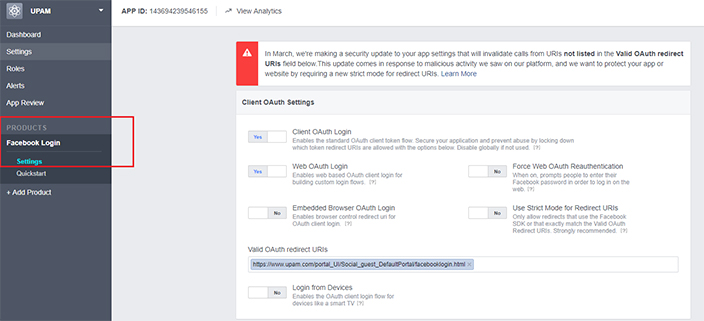
9. Paste
the Facebook Authorized Origins information as directed
into the Valid OAuth
redirect URLs Field.
10. Save
all changes.
You can now use Facebook for UPAM Authentication.
Configuring the
Google API
1. Go
to https://console.developers.google.com/apis/credentials?project=mimetic-surf-155906.
Click on the Select a
project drop-down at the top of the screen, then click on the
Add icon on
the Select window.
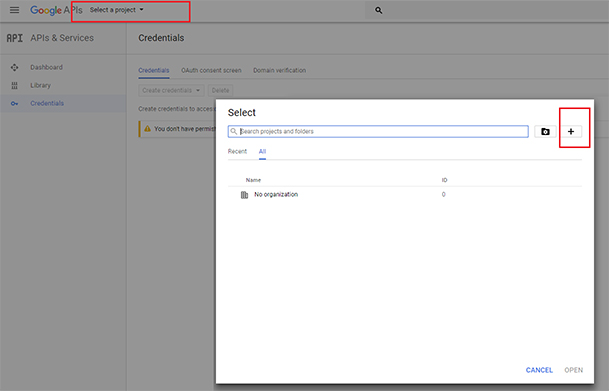
2. On
the New Project Screen, enter the name of your project (e.g., UPAM Test) and
click Create.
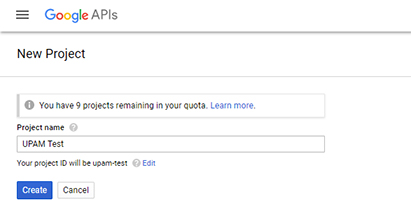
3. Click on the Select a
project drop-down at the top of the screen, then click on the
project you just created (e.g., UPAM Test).
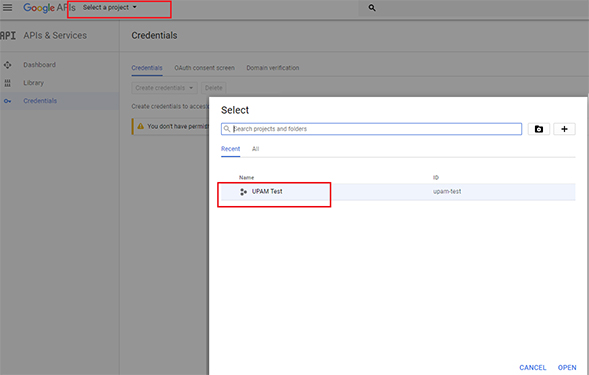
4. Click
on Create credentials and select OAuth client ID,
as shown as below.
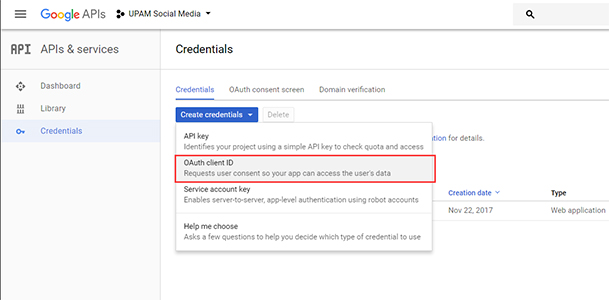
5. On
the Create Client ID Screen, select “Web Application”. Enter the Project Name
and Authorized JavaScript origins. (Defined in the local DNS, directed to the
UPAM Portal IP, it is the Portal Server Domain name in the Guest Access
Strategy.) Click Create.
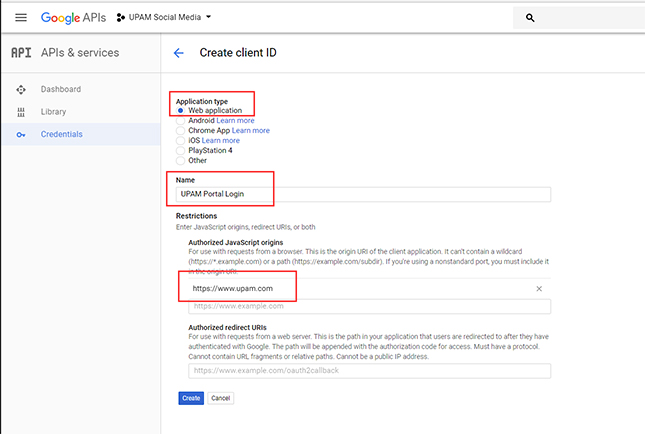
The Client ID and Client Secret are displayed.
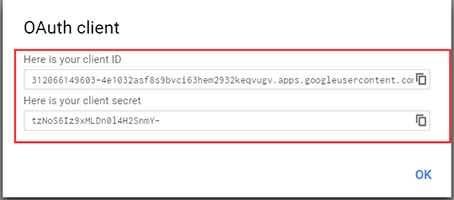
6. Go
to the Guest Access Strategy Screen in OmniVista (UPAM - Guest Access - Guest
Access Strategy)
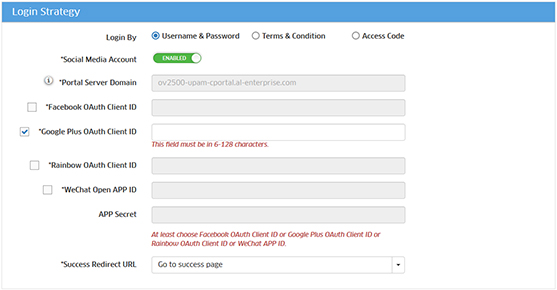
7. In the Google
Plus OAuth Client ID field, enter the Client ID you
received from Google.
8. Return
to the Google API Configuration Screen.
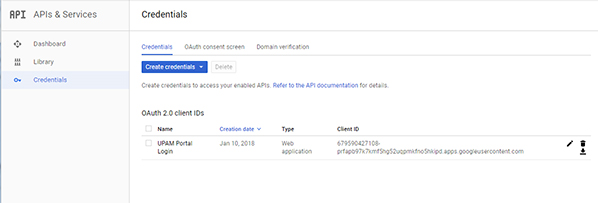
9. Click on the Edit icon next to
the OAuth 2.0 client ID you just created.
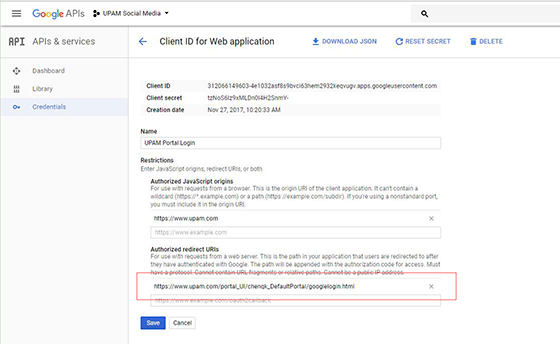
10. Paste
the Google Authorized Origins information as directed
into the Authorized redirect URLs Field and click Save.
11. Enable Google + API service on Google API developer to receive requests from OV
during UPAM authentication. Click on Dashboard in the Navigation Tree, then click on Enable
APIs and Services.
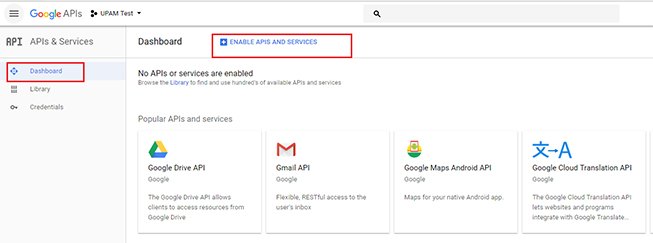
12. Select Social in the "Filter by" List on the right side of the screen.
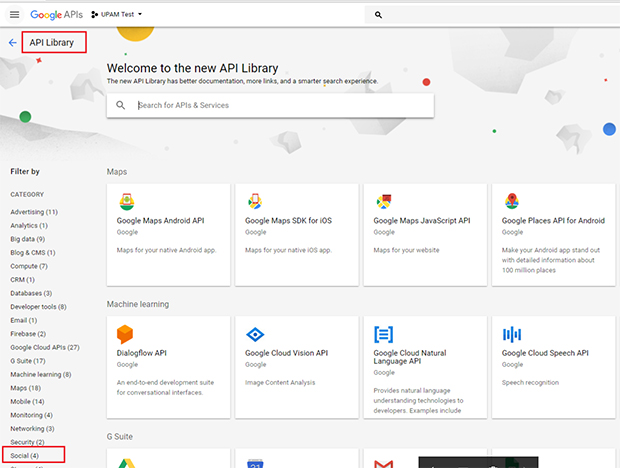
13. Select Google+ API.
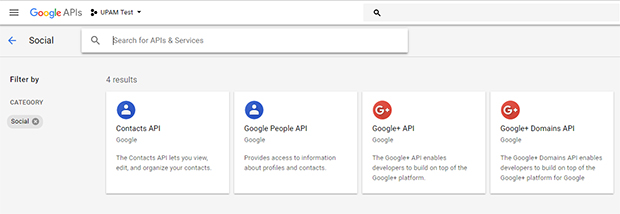
14. Click Enable.
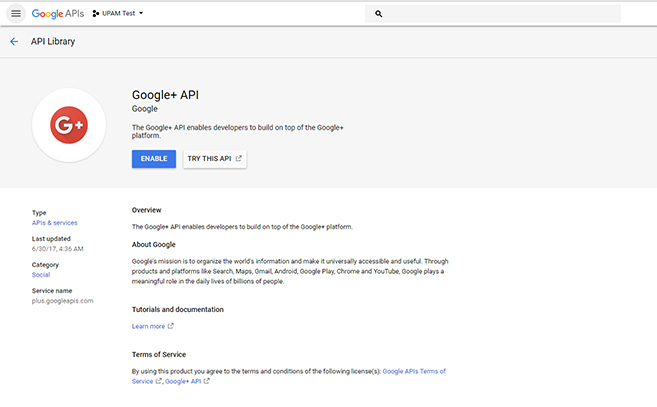
You can now use Google for UPAM Authentication.
Configuring the
Rainbow API
1. Set https://www.openrainbow.com and https://web.openrainbow.com in the Allowlist in OmniVista.
2. If you do not have a Rainbow account, go to https://hub.openrainbow.com/#/dashboard/overview and create one.
3. After creating an account, go to the Developers Applications page and click on the Create New Application button.
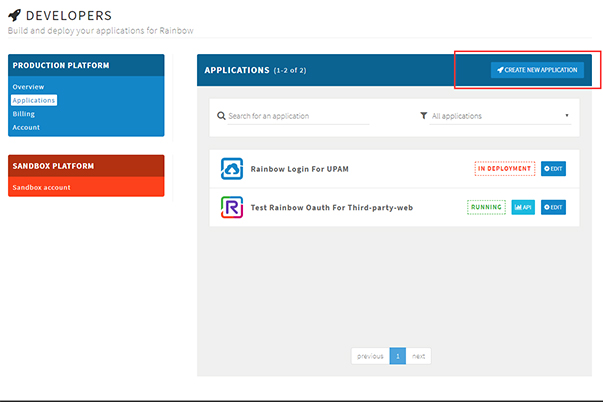
4. In the Main Information section go to the Target drop-down and select Web application.
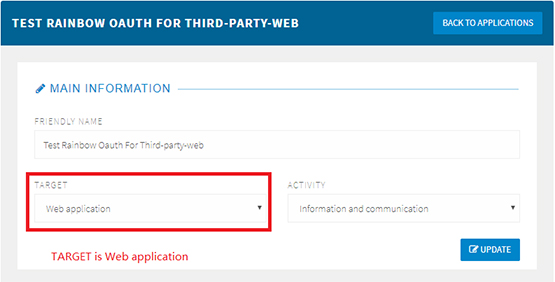
5. In the OAOTH 2.0 Information section, add the Guest Portal page URL.
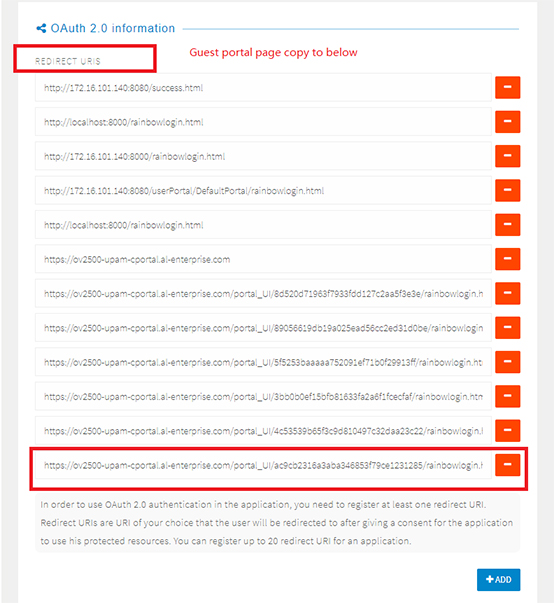
6. Under OAUTH 2.0 Implicit Grant section, enable OAUTH 2.0 Implicit Grant.
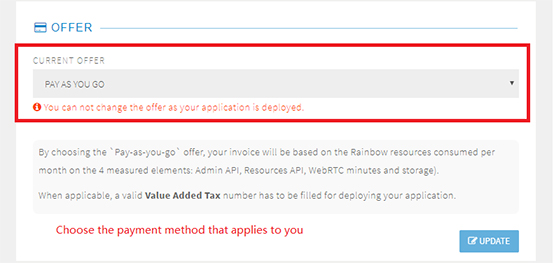
7. In the Offer section, choose a payment method.
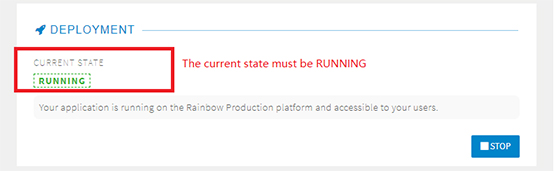
8. In the Deployment section, make sure the Current State is Running.
9. Go
to the Guest Access Strategy Screen in OmniVista (UPAM - Guest Access - Guest
Access Strategy).
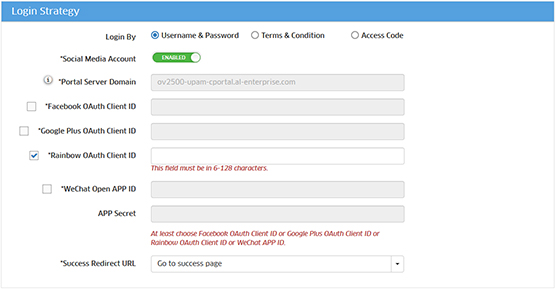
10. In the Rainbow 0Auth
Client ID field, enter the Rainbow App ID that you receive from Rainbow.
11. Open the Portal page and login using Rainbow.
12. Enter the Rainbow App ID in the Rainbow Application field on the Guest Access Strategy page in OmniVista.
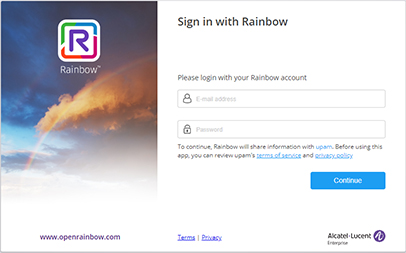
13. When you open the Portal Page, click on Sign in with Rainbow and sign into your Rainbow account.

14. On the UPAM Authorization page, click on Authorize.
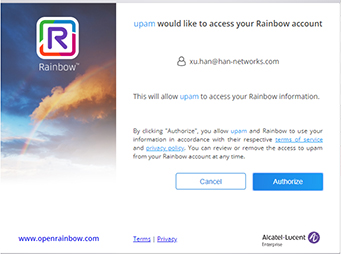
The following login message will appear.
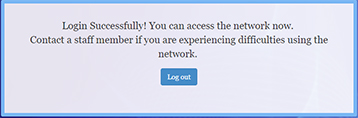
You can now use Rainbow for UPAM Authentication. For more information, go to the Rainbow Documentation Core Concepts page.
Configuring the
WeChat API
1. Go to the WeChat website (https://mp.weixin.qq.com) and click on Register Now to create a Service Account.
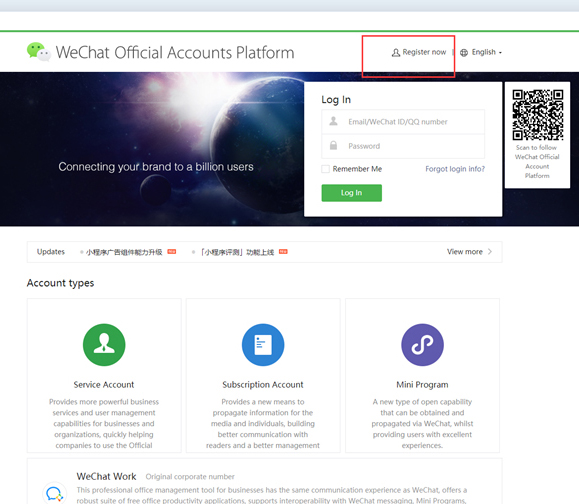
2. After creating the account, login and add plug-ins from the WeChat Store and WiFi.
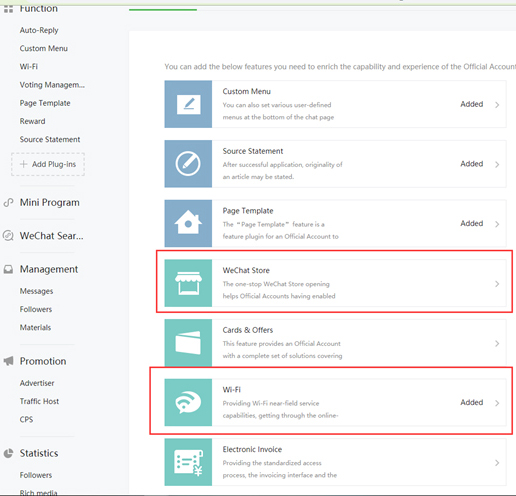
3. To use WiFi, you must create a store In the WeChat Store Plugins.
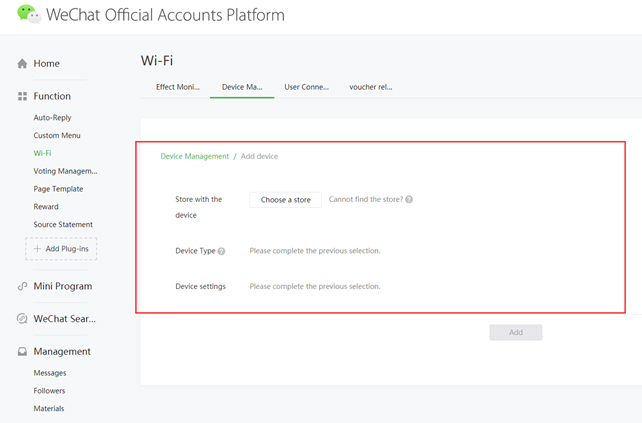
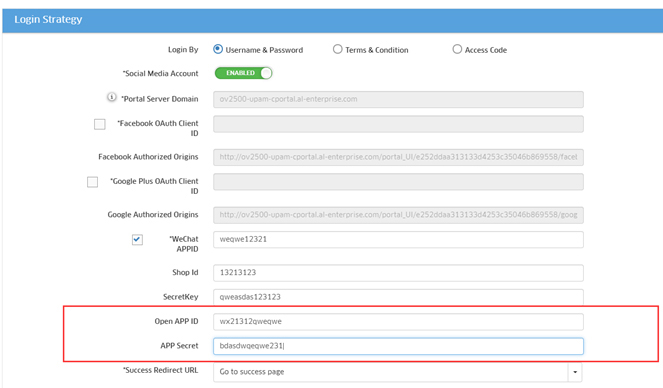
4. You will receive the WeChat social login parameters that must be entered into the UPAM Guest Access Strategy Screen:
- Store Name
- SSID
- shopId
- appId
- secrectKey
5. Go
to the Guest Access Strategy Screen in OmniVista (UPAM - Guest Access - Guest
Access Strategy).
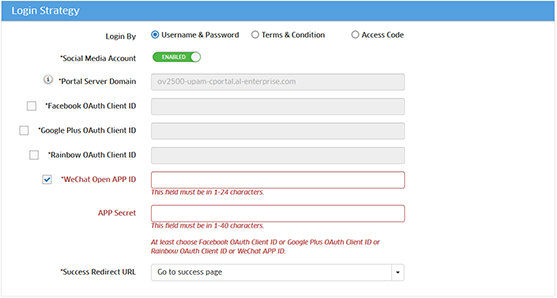
6. Enter the required WeChat information on the Guest Access Strategy Screen in OmniVista.
You can now use WeChat for UPAM Authentication on Smartphone and iPad devices. If want to use WeChat authentication on PCs/Laptops, you must complete Steps 6 - 10.
7. Login to WeChat (https://mp.weixin.qq.com).
8. Create a website application.
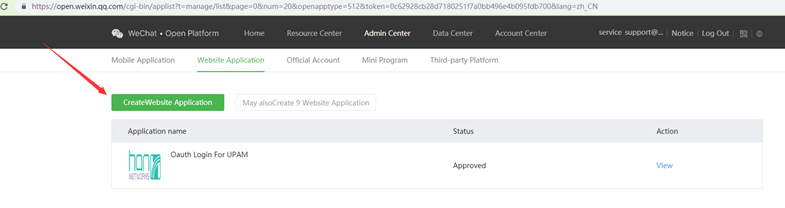
9. You will receive an application.
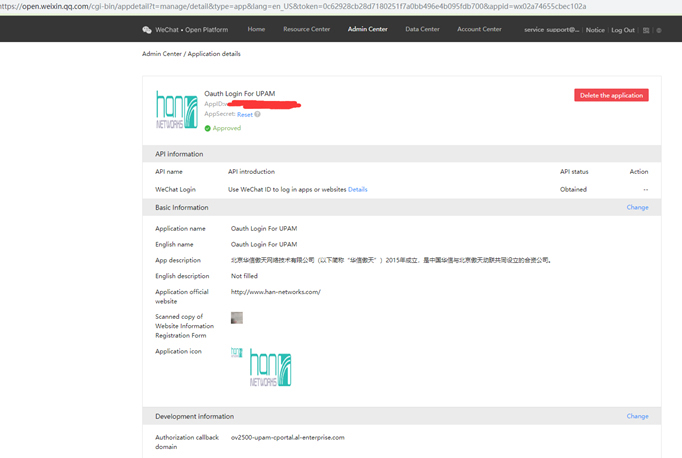
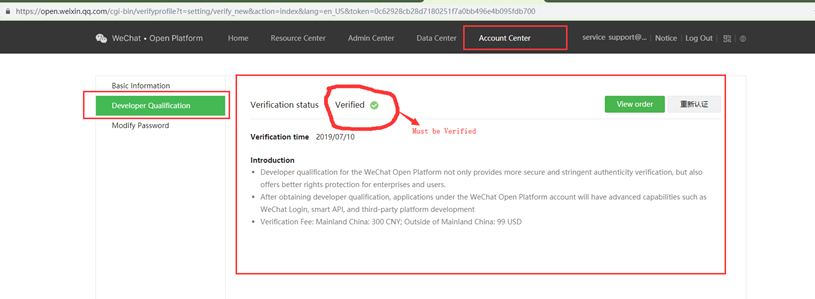
10. If API status is not obtained, you must pay to receive "Verified" status.
11. The Authorization callback domain of the WeChat website application should be populated with your portal server domain (Current FQDN of the Guest Strategy, which is the UPAM server). Then copy AppID and AppSecret in your WeChat web app to the Guest Strategy page, as shown below.